The rEFInd Boot Manager:
Managing Secure Boot
by Roderick W. Smith, rodsmith@rodsbooks.com
Originally written: 11/13/2012; last Web page update:
12/5/2012, referencing rEFInd 0.5.0
I'm a technical writer and consultant specializing in Linux technologies. This Web page is provided free of charge and with no annoying outside ads; however, I did take time to prepare it, and Web hosting does cost money. If you find this Web page useful, please consider making a small donation to help keep this site up and running. Thanks!
| Donate $1.00 |
Donate $2.50 |
Donate $5.00 |
Donate $10.00 |
Donate another value |
|
|
|
|
|
|
This page is part of the documentation for the rEFInd boot manager. If a Web search has brought you here, you may want to start at the main page.
If you're using a computer that supports Secure Boot, you may run into extra complications. This feature is intended to make it difficult for malware to insert itself early into the computer's boot process. Unfortunately, it also complicates multi-boot configurations such as those that rEFInd is intended to manage. This page describes some secure boot basics and two specific aspects of rEFInd and its interactions with Secure Boot: installation issues and known bugs and limitations in rEFInd's Secure Boot features.
Basic Issues
Through 2012, it became obvious that Secure Boot would be a feature that was controlled, to a large extent, by Microsoft. This is because Microsoft requires that non-server computers that display Windows 8 logos ship with Secure Boot enabled. As a practical matter, this also means that such computers ship with Microsoft's keys in their firmware. In the absence of an industry-standard body to manage the signing of Secure Boot keys, this means that Microsoft's key is the only one that's more-or-less guaranteed to be installed on the computer, thus blocking the ability to boot any OS that lacks a boot path through Microsoft's signing key.
Fortunately, Microsoft will sign third-party binaries with their key. A payment of $99 to Verisign enables a software distributor to sign as many binaries as desired. Red Hat (Fedora), Novell (SUSE), and Canonical (Ubuntu) have all announced plans to take advantage of this system. Unfortunately, using a third-party signing service is an awkward solution for open source software. In fact, for this very reason Red Hat has developed a program that it calls shim that essentially shifts the Secure Boot "train" from Microsoft's proprietary "track" to one that's more convenient for open source authors. Shim is signed by Microsoft and redirects the boot process to another boot loader that can be signed with keys that the distribution maintains and that are built into shim. Fedora 18 is expected to use this system. SUSE has announced that it will use the same system, as does Ubuntu with version 12.10 and later. SUSE has contributed to the shim approach by supporting a set of keys that users can maintain themselves. These keys are known as Machine Owner Keys (MOKs), and managing them is described later, in Managing MOKs. To reiterate, then, there are potentially three ways to sign a binary that will get it launched on a system that uses shim:
- Secure Boot keys—These keys are managed by the EFI firmware. In a default configuration, Microsoft is the only party that's more-or-less guaranteed to be able to sign boot loaders with these keys; however, it's possible to replace Microsoft's keys with your own, in order to take full control of Secure Boot on your computer. The trouble is that this process is tedious and varies in details from one computer to another.
- Shim's built-in keys—It's possible, but not necessary, to compile shim with a built-in public key. Its private counterpart can then be used to sign binaries. In practice, this key type is limited in utility; it's likely to be used by distribution maintainers to sign their own version of GRUB and the Linux kernels that it launches, nothing more. On the plus side, shim's keys require little or no maintenance by users. One potential complication is that if you swap out one shim binary for another, its built-in key may change, which means that the replacement shim might no longer launch its follow-on boot loader.
- MOKs—Versions 0.2 and later of shim support MOKs, which give you the ability to add your own keys to the computer. If you want to install multiple Linux distributions in Secure Boot mode, MOKs are likely to be helpful. They're vital if you want to launch kernels you compile yourself or use boot managers or boot loaders other than those provided by your distribution.
All three key types are the same in form—shim's built-in keys and MOKs are both generated using the same tools used to generate Secure Boot keys. Unfortunately, the tools used to generate these keys are still rather crude and are rarely installed on Linux systems, which is one of the reasons that rEFInd's installation script doesn't yet support setting up a Secure Boot configuration. Although it's theoretically possible to use rEFInd without signing your own binaries, this is not yet practical, because distributions don't yet provide their own signed binaries or the public MOK files you must have to enroll their keys. With any luck this will change in 2013. At the very least, many distributions will begin supporting Secure Boot in the near future, and with any luck they'll include their public MOKs for use with other distributions' versions of shim.
Because shim and MOK are being supported by several of the major players in the Linux world, I've decided to do the same with rEFInd. Beginning with version 0.5.0, rEFInd can communicate with the shim system to authenticate boot loaders. If a boot loader has been signed by a valid UEFI Secure Boot key, a valid shim key, or a valid MOK key, rEFInd will launch it. rEFInd will also launch unsigned boot loaders or those with invalid signatures if Secure Boot is disabled in or unsupported by the firmware. (If that's your situation, you needn't bother reading this page.)
Version 0.5.0 doesn't yet ship in a pre-signed form; you'll need to create your own keys, as described shortly, and use them to sign your binary of rEFInd. I'm forcing you to do this because it's necessary to sign your post-rEFInd binaries anyhow.
Installation Issues
A working Secure Boot installation of rEFInd involves at least three programs, and probably four or more, each of which must be installed in a specific way:
- shim—You can download a version of shim signed with Microsoft's Secure Boot key here. This version (created by shim's developer, Matthew J. Garrett) includes a shim key that's signed nothing but the MokManager.efi program that also ships with the program. Thus, to use this version of shim, you must use MOKs. Ubuntu 12.10 ships with its own shim, but that version doesn't support MOKs and so is useless for launching rEFInd. Future versions of Fedora, SUSE, and probably other distributions will come with their own variants of shim, most of which will no doubt support their own shim keys as well as MOKs. You should install shim just as you would install other EFI boot loaders, as described here.For use in launching rEFInd, it makes sense to install shim.efi in EFI/refind on your ESP, although of course this detail is up to you.
- MokManager—This program is included with shim 0.2 and later. It presents a crude user interface for managing MOKs, and it's launched by shim if shim can't find its default boot loader (generally grubx64.efi) or if that program isn't properly signed. In principle, this program could be signed with a MOK, but the binary in Garrett's shim 0.2 is signed with a shim key, and I expect that versions distributed with most Linux distributions will also be signed by their respective shim keys. This program should reside in the same directory as shim.efi, under the name MokManager.efi. Although you could theoretically do without MokManager, in practice you'll need it at least temporarily to install the MOK with which rEFInd is signed.
- rEFInd—Naturally, you need rEFInd. Because shim is hard-coded to launch a program called grubx64.efi, you must install rEFInd using that name and to the same directory in which shim.efi resides. In theory, rEFInd could be signed with a Secure Boot key, a shim key, or a MOK; however, because Microsoft won't sign binaries distributed under the GPLv3, I can't distribute a version of rEFInd signed with Microsoft's Secure Boot key; and as I don't have access to the private shim keys used by any distribution, I can't distribute a rEFInd binary signed by them. Thus, rEFInd will normally be signed by a MOK. As of version 0.5.0, you must sign your rEFInd binary with your own MOK.
- Your boot loaders and kernels—Your OS boot loaders, and perhaps your Linux kernels, must be signed. They can be signed with any of the three key types. Indeed, your system may have a mix of all three types—a Windows 8 boot loader will most likely be signed with Microsoft's Secure Boot key, GRUB and kernels provided by most distributions will be signed with their own shim keys, and if you use your own locally-compiled kernel or a boot loader from an unusual source you may need to sign it with a MOK. Aside from signing, these files can be installed in exactly the same way as if your computer were not using Secure Boot.
Because of variables such as which version of shim you're using, I can't provide an absolutely complete procedure for installing rEFInd to work with Secure Boot. Broadly speaking, though, the procedure should be something like this:
- Boot the computer. This can be a challenge in and of itself. You may need to use a Secure Boot–enabled Linux emergency disc, temporarily disable Secure Boot, or do the work from Windows.
- Download shim from Matthew J. Garrett's download site or from your distribution. (Don't use Ubuntu 12.10's version, though; as noted earlier, it's inadequate for use with rEFInd.)
- Copy the shim.efi and MokManager.efi binaries to the directory you intend to use for rEFInd—for instance, EFI/refind on the ESP.
- If it's not already installed, install OpenSSL on your computer. (It normally comes in a package called openssl.
- Type the following two commands to generate your public and private keys:
$ openssl req -new -x509 -newkey rsa:2048 -keyout MOK.key -out MOK.crt \
-days 3650 -subj "/CN=Your Name/"
$ openssl x509 -in MOK.crt -out MOK.cer -outform DER
Change Your Name to your own name or other identifying characteristics, and adjust the certificate's time span (set via -days as you see fit. After you type the first command, it will prompt you for a passphrase. Remember this, since you'll need it to sign your binaries. The result is a private key file (MOK.key), which is highly sensitive since it's required to sign binaries, and two public keys (MOK.crt and MOK.cer), which can be used to verify signed binaries' authenticity.
- Copy the three key files to a secure location and adjust permissions such that only you can read MOK.key. You'll need these keys to sign future binaries, so don't discard them.
- Copy the MOK.cer file to your ESP, ideally to a location with few other files.
- Download and install the sbsigntool package. Binary links for various distributions are available from the OpenSUSE Build Service, or you can obtain the source code by typing git clone git://kernel.ubuntu.com/jk/sbsigntool.
- Sign the rEFInd binary by typing sbsign --key MOK.key --cert MOK.crt --output grubx64.efi refind_x64.efi, adjusting the paths as necessary to the keys and the rEFInd binary. Note that you're giving the signed rEFInd binary the filename grubx64.efi. This is necessary to launch rEFInd from shim.
- Follow the manual installation instructions for rEFInd on the Installing rEFInd page; however, give rEFInd the filename grubx64.efi and register shim.efi with the EFI by using efibootmgr in Linux or bcdedit in Windows.
- Reboot. With any luck, you'll see a simple text-mode user interface with a label of Shim UEFI key management. This is the MokManager program, which shim launched when rEFInd failed verification because its key is not yet enrolled.
- Press your down arrow key and press Enter to select Enroll key from disk. The screen will clear and prompt you to select a key, as shown here:
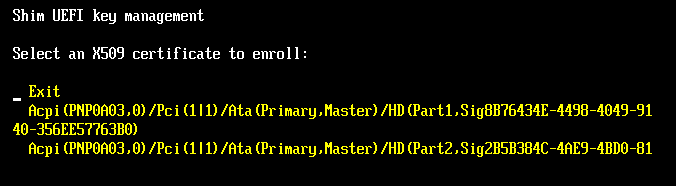
- Each of the lines with a long awkward string represents a disk partition. Select one and you'll see a list of files. Continue selecting subdirectories until you find the MOK.cer file you copied to the ESP earlier.
- Select MOK.cer. You can type 1 to view your certificate's details if you like, or skip that and type 0 to enroll the key.
- Back out of any directories you entered and return to the MokManager main menu.
- Select Continue boot at the main menu.
At this point the computer may boot into its default OS, reboot, or perhaps even hang. When you reboot it, though, rEFInd should start up in Secure Boot mode. It should now be able to launch any boot loader signed with a key recognized by the firmware or by shim (including any MOKs you've enrolled). If you want to manage keys in the future, rEFInd displays a new icon in the second (tools) row you can use to launch MokManager. (This icon appears by default, but if you edit showtools in refind.conf, you must be sure to include mok_tool as an option in order to gain access to it.)
If you're using Ubuntu 12.10, you can't use its version of shim, but you can replace it with Garrett's shim. The problem is that Ubuntu's GRUB and kernel will then be signed by an unknown key. Unfortunately, I haven't found a suitable public key file on Ubuntu's distribution medium, so you may need to sign GRUB and/or your kernels with your own MOK. In principle, you should be able to use shim 0.2 or later from future distributions that include it; but you must be sure that whatever you use supports MokManager.
Secure Boot Caveats
rEFInd's Secure Boot support is brand-new with version 0.5.0 of the program. Unfortunately, rEFInd, like shim, must essentially bypass UEFI security features, and must simultaneously not create security problems, in order to work. Unfortunately, the procedures that rEFInd uses to do this (which were lifted straight from shim) play "fast and loose" with the UEFI rules. This fact creates a number of limitations, which include (but are almost certainly not limited to) the following:
- rEFInd can launch one shim/MOK-signed driver, no more. If you
try to launch two drivers, rEFInd throws up an Access Denied
error for the second driver.
- ELILO can't find its configuration file when launched from rEFInd in
Secure Boot mode. The same may be true of GRUB or other boot loaders,
but I haven't tested them.
- Under certain circumstances, the time required to launch a boot loader
can increase. This is unlikely to be noticeable for the average small
boot loader, but could be significant for larger boot loaders on slow
filesystems, such as Linux kernels on ext2fs, ext3fs, or ReiserFS
partitions.
- I haven't tested launching Windows from rEFInd in Secure Boot mode.
This is admittedly a huge omission; but I don't have a suitable
installation for testing.
- Secure Boot mode doesn't work on x86 (IA32) or ARM systems, just
on x86-64 (AMD64) computers. This is largely because shim has
the same limitations.
My focus in testing rEFInd's Secure Boot capabilities has been on getting Linux kernels with EFI stub loaders to launch correctly.
At the moment, I consider rEFInd's shim/MOK support to be of alpha quality. I'm releasing it in this state in the hope of getting feedback from adventurous early adopters. I expect the improve the installation procedure, and with any luck fix some of the known bugs, in the next couple of versions. Some of the usability improvements are dependent upon MOK-capable versions of shim being released with major distributions; such versions of shim, with kernels signed with the key that matches the one built into shim, will greatly reduce the need for users to sign boot loaders.
copyright © 2012 by Roderick W. Smith
This document is licensed under the terms of the GNU Free Documentation License (FDL), version 1.3.
If you have problems with or comments about this Web page, please e-mail me at rodsmith@rodsbooks.com. Thanks.
Go to the main rEFInd page
Learn about rEFInd's history
Return to my main Web page.
